Another puzzle we solved late into the piece. We had a TGZ file containig two things a PCAP file and a Clue.txt.
The PCAP file contained a single packet with the following data inside:
root@kali:~/pragyan/forensics/crack-this# tcpdump -r problem.pcap -A
reading from file problem.pcap, link-type EN10MB (Ethernet)
05:59:54.303760 IP localhost.32769 > localhost.9600: UDP, length 20
E..0..@.@.<...........%.....rukgzuzfiuypreymqcja
The Clue.txt had just the following seemingly redundant information:
root@kali:~/pragyan/forensics/crack-this# cat Clue.txt
IP - 127.0.0.1
Port - 32769
We analysed the cipher with Crypto Crack tool and it gave us these suggested ciphers to try:
IC: 32, Max IC: 125, Max Kappa: 188
Digraphic IC: 0, Even Digraphic IC: 0
3-char repeats: 0, Odd spaced repeats: 50
Avg digraph: 375, Avg digraph discrep.: 110
Most likely cipher type has the lowest score.
Running Key............14
6x6 Bifid..............22
Period 7 Vigenere......24
Beaufort...............25
Patristocrat...........25
Porta..................25
Porta stood out since the “Clue.txt” specifically says “Port” but nonetheless i tried all of them. Eventually trying a dictionary attack using each and stumbling upon a partial decryption using the key “local”:
- maythcftvcgidrgrjqws
Given the other Star Wars related flags so far my eyes were quick to spot this. I checked the key and put 2 + 2 together. The clue with the 127.0.0.1 address, 127.0.0.1 -> “localhost”.
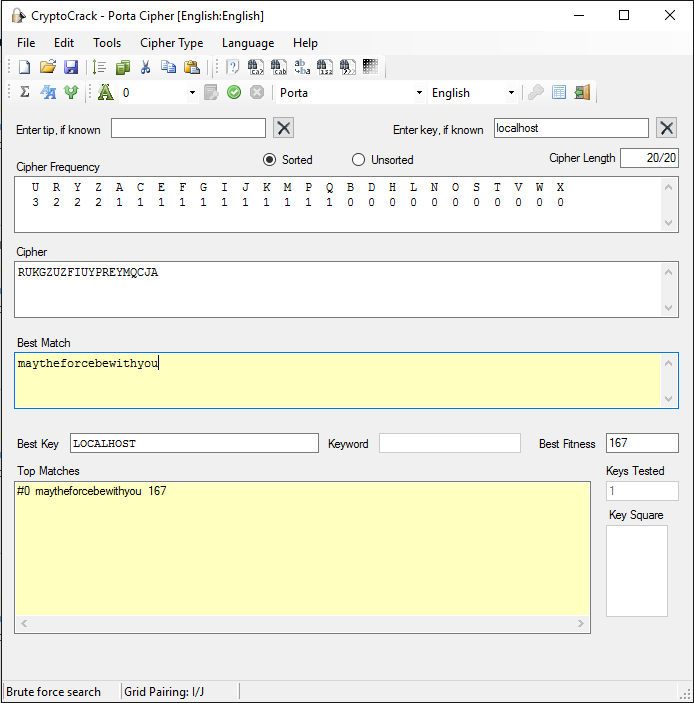
I tried a decryption using Porta, with key = localhost and got the flag:
- maytheforcebewithyou