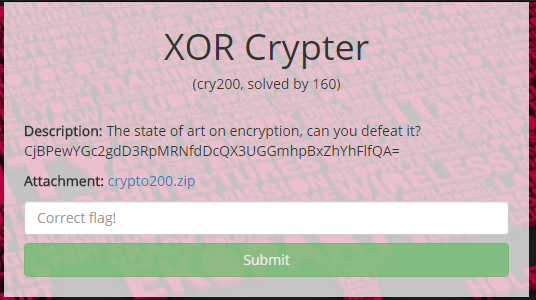
Very quick challenge this one, solved in one line shell script. Here’s the clue:
The ZIP file contains a Python script called “shiftcrypt.py”. The meat is this part:
result = []
blocks = struct.unpack("I" * (len(data) / 4), data)
print repr(blocks)
for block in blocks:
result += [block ^ block >> 16]
The first thing I thought here is, this is not right? We can just do the same operation and get back the original data yes?
Let’s try, we take the string they gave us to decrypt:
- CjBPewYGc2gdD3RpMRNfdDcQX3UGGmhpBxZhYhFlfQA=
And we make it encrypt it again:
root@mankrik:~/ekoparty/crypto200# echo CjBPewYGc2gdD3RpMRNfdDcQX3UGGmhpBxZhYhFlfQA= | base64 -d > c; ./shiftcrypt.py "`cat c`" | tail -1 | base64 -d
EKO{unshifting_the_unshiftable}
There we go, our flag: EKO{unshifting_the_unshiftable}