HUST festival was this weekend and we participated although many parts of the festival were Korean language, they made a great effort to put English clues in for all the challenges.
This challenge was one of the earliest available so we tackled it first. It was pretty much just a PCAP file with instructions to connect to an IP address on port 22.
We downloaded the file, unzipped it and found the PCAP to be pretty large in size:
root@mankrik:~/hust/net300# unzip net_7be01f8e.zip
Archive: net_7be01f8e.zip
inflating: league_of_access.pcap
root@mankrik:~/hust/net300# file league_of_access.pcap
league_of_access.pcap: pcap-ng capture file - version 1.0
root@mankrik:~/hust/net300# ls -lah league_of_access.pcap
-rw-r--r-- 1 root root 9.1M May 22 15:09 league_of_access.pcap
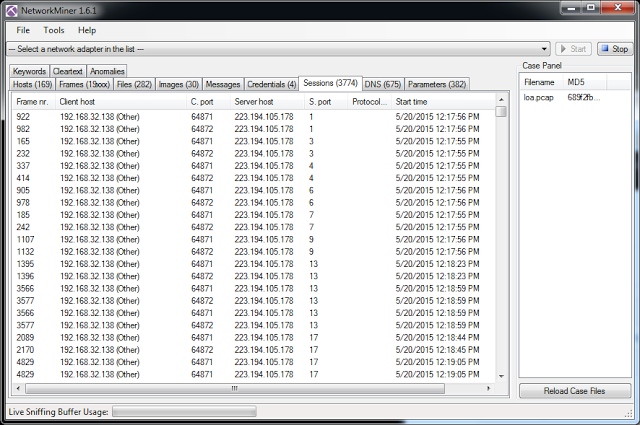
Whenever I have a bigger PCAP I use a Windows program called Network Miner to get a graphical overview of different attributes of the traffic in the PCAP. Network Miner needs a PCAP file (i.e. not a PCAP-NG file) so I used Wireshark to “Save As” a PCAP file before importing it into Network miner.
In Network Miner, I used the Session window to sort the connections found in the PCAP by different attributes. I sorted by “Server Port” column to notice that the user conducted a port scan against the target server
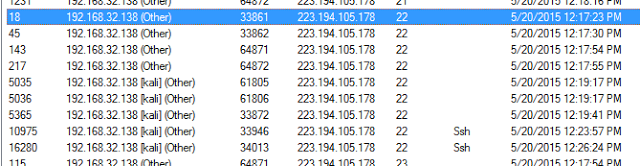
I then checked the SSH connections and noted the timestamps of the connections. I noted that the final SSH connection attempts happened some minutes after the port scan completed.
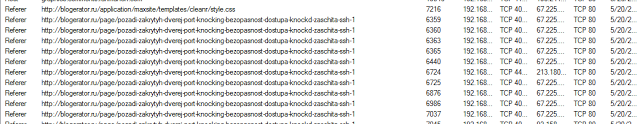
I then examined some of the other tabs in Network miner. In the Parameters window I noticed quite a few Referrer entries from a Russian blog post about “port knocking”:
I also found some more “port knocking” hints in the DNS tab:
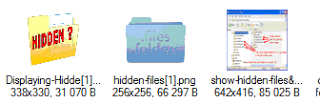
Lastly, there was a couple of other things I noted in the images tab, a few items mentioning “hidden files”:
Ok so now I feel it’s time to switch over to Wireshark because I have a good idea of the method of attack here:
- Port knocking, to open an SSH port
- Hidden files on the host
In Wireshark I setup a filter to just examine traffic to/from this host in question:
- “ip.src == 223.194.105.178 or ip.dst == 223.194.105.178”
Next, I scrolled down to the Frame #’s shown during the Network Miner investigation to see if the user was able to successfully get that SSH fired up.
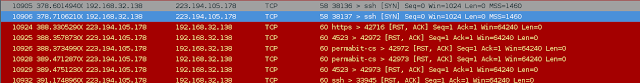
First I double checked that the user was still getting failed SSH connections, and at Frame # 10905 & 10932 I see a failed connection attempt.
Then later, at frame 10967 & 10968 a successful connection is found:
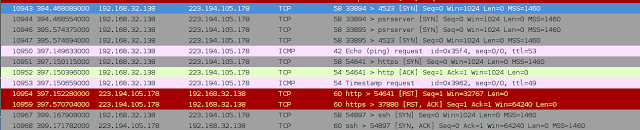
So what changed between 10905 and 10967? Well we’re thinking port knocking so let’s see if we can see a weird bunch of connection attempts before this and see the following:
At this point im not 100% sure which of these are port knocking and which is just coincidental traffic. So I decided to try all of it. I came with the following command line:
root@mankrik:~/hust/net300# nmap -sS -p T:80,4523,2351,2351,4523,443 223.194.105.178; ping -c 1 -t 1 223.194.105.178; icmpush -tstamp -seq 0 -id 13970 -to 1 223.194.105.178; ssh you@223.194.105.178
Which actually worked first go. So either I got right or I got lucky.
Anyway, once on the server getting the flag was pretty simple. Using the clue of “hidden” files I expected there to be a file beginning with “.” and sure enough there was:
-bash-4.1$ find
.
./.bashrc
./.bash_logout
./.bash_profile
./.bashc
./.bash_history
-bash-4.1$ id
uid=500 gid=500(you) groups=500(you)
-bash-4.1$ cat .bashc
++++++++++++++++++++++++++++++++++
++++++++++++++++++++++++++++++++++
++++++++-----------------+++++++++
+++++++| |++++++++
+++++++| Hari60_iz_B3s+! |++++++++
+++++++| |++++++++
++++++++-----------------+++++++++
++++++++++++++++++++++++++++++++++
++++++++++++++++++++++++++++++++++
-bash-4.1$ exit