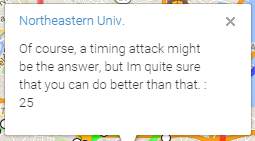
This challenge was the third on the School Bus line in Boston Key Party 2015. The clue was as below and the challenge was worth 25 points.
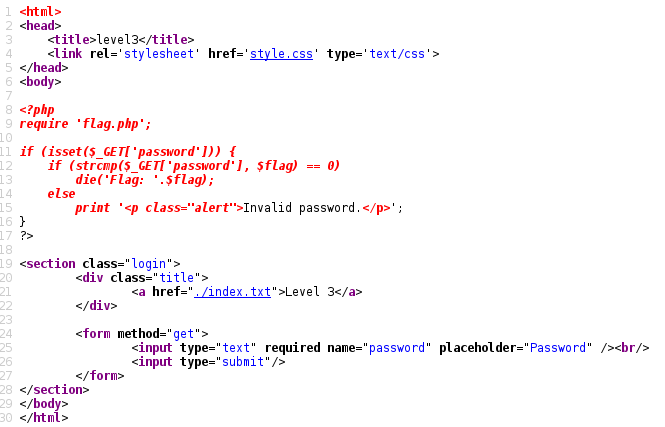
The link in the clue lead to a URL which, when the source was viewed lead to a second page that gave us a look at the PHP source code for the site which you can see below:
At first glance it seems that the flag itself is the password and that this code is expecting you to know the flag before you get the flag. That sounds counter intuitive so there must be a deeper explanation here.
Since there’s only one mechanism in place (strcmp) we decided to investigate further. As it turns out strcmp is a poor choice when used to validate user input, especially, as in this case, when combined with a loose validation (== vs. ===) as it can easily be tricked into returning NULL which will evaluate to 0 for the purposes of the above script. Firstly, according to the PHP documentation the return values of strcmp are:
Returns < 0 if str1 is less than str2; > 0 if str1 is greater than str2, and 0 if they are equal.
However what’s missing here is that strcmp will return NULL or 0 in many other scenarios when type conversions result in something unexpected.
This is known as a strcmp bypass and there is a fairly decent writeup on this class of vulnerability over on this blog linked here.
So in order to bypass the strcmp we used Burpsuite to intercept the form data and modify the GET request to be: username=a&password[]=0
Since this comparison cannot be successfully completed by strcmp (strcmp expects a string but got an array instead), it will return a value == 0 and the test on line 12 of the code will pass and we are handed our flag.